#1 in Shadow IT Discovery & Action
The most advanced discovery platform helps you understand and optimize your app usage, software spend, and drive employee productivity
By the numbers
Most of your tech stack is hiding in the shadows
50%
of SaaS tech stacks are provisioned outside of IT
Source: Microsoft
5x
your known SaaS stack lives in the shadows
Source: Torii Customer Data
99%
of cloud breaches are caused by application or user configuration errors
Source: Gartner
How Torii illuminates Shadow IT
10,000+ Apps
Industry-leading 113+ direct integrations reach 10,000 additional cloud apps via 2nd-degree discovery
Continuous Endpoint Detection
Spot Shadow IT immediately when it happens at user endpoints without lifting a finger
Highest Accuracy
Get the most complete picture by combining SSO, identity, expense, HR and other sources in one view
Find Every App
See sanctioned and Shadow IT apps in one unified view
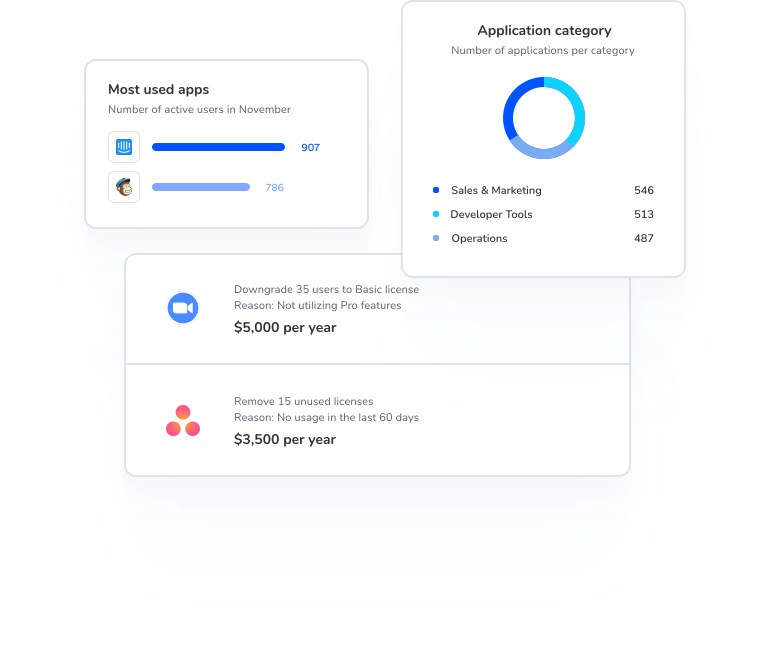
“With Torii, we could finally see every single SaaS tool we were using in the company. It enabled us to review their popularity and usage, determine which applications were redundant and which ones we could cut down.”
Ron Peres
Sr. Director, Global Corporate IT & Information Systems
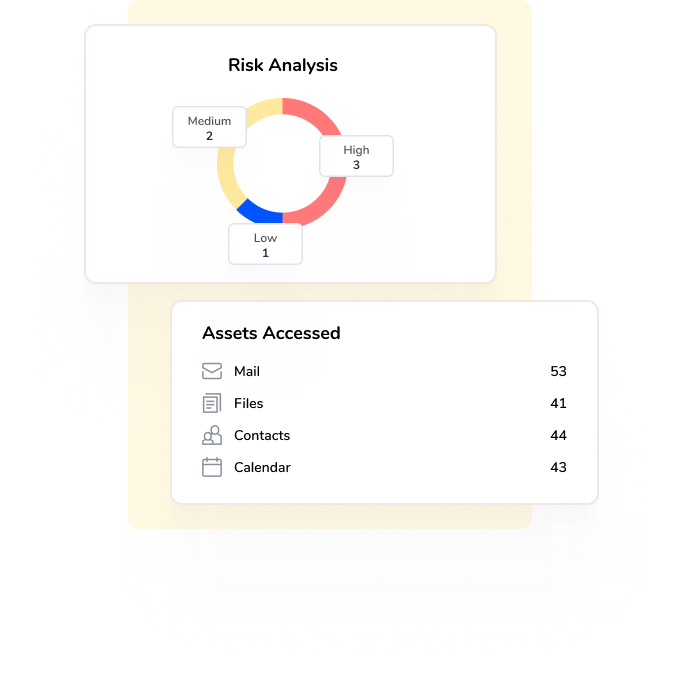
Shadow IT Risk Mapping
Identify risky apps in your Shadow IT portfolio based on their permissions to modify sensitive data
Don't just see Shadow IT: do something about it
Act & Automate
Create custom alerts, communications and automation for any Shadow IT scenario
De-Risk your Shadow Stack
Get notified as soon as a new Shadow IT app and quickly understand their risk amp
Eliminate Shadow IT waste
Take control of Shadow IT spend and renewals by instantly connecting with app owners and co-managing apps
Torii's customers have:
3x
Discovered that the number of SaaS apps in use is 3x higher than they initially thought
$1m
Saved more than $1m a year on unused SaaS accounts
75%
Cut hours spent on manual IT tasks by at least 75%
See Torii in Action
Learn how Torii can automate your SaaS management.