The Agentic Governance Platform for SaaS & AI
The sprawl stops here. Whether it’s apps, access, or identities, Torii’s SMP and IGA solutions help you see it, control it, and secure it.
Trusted by the best.
Manage Your SaaS & Identities in One Place
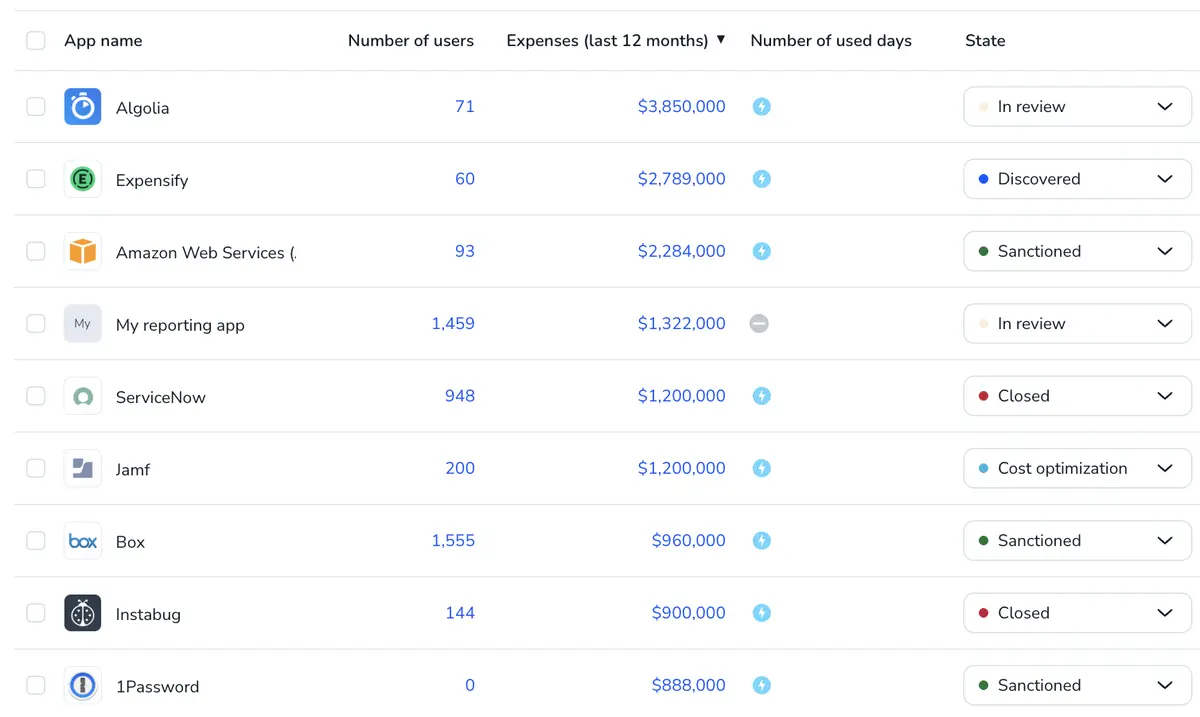
Continuous App Discovery
Discover SaaS, AI, and desktop apps continuously across your estate.
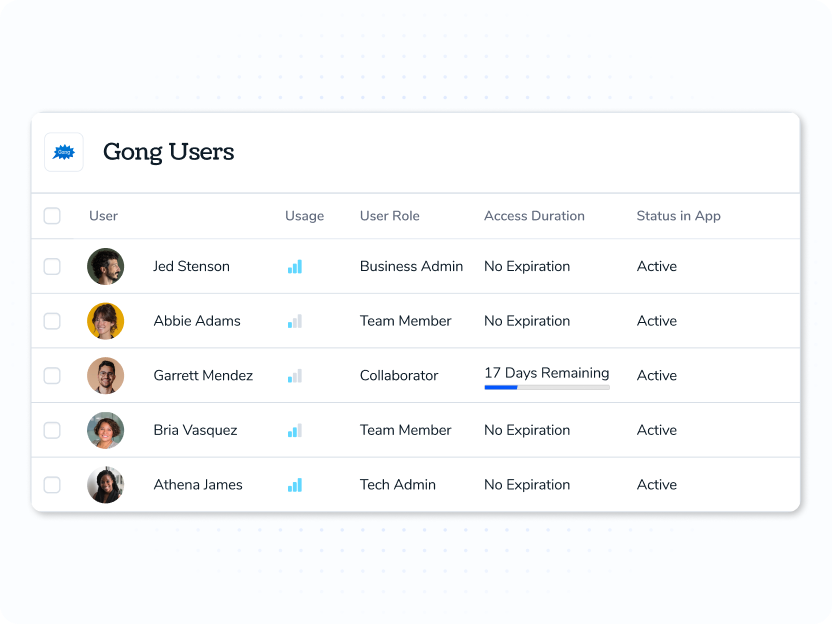
Resolve human and machine identities and map accounts and entitlements.
Surface real usage and ownership to right-size access and deprovision fast.
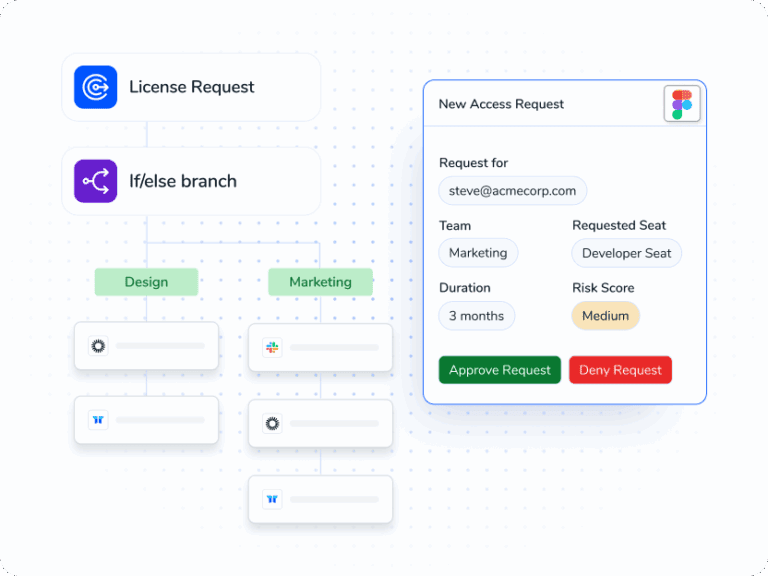
Seamless Access Management
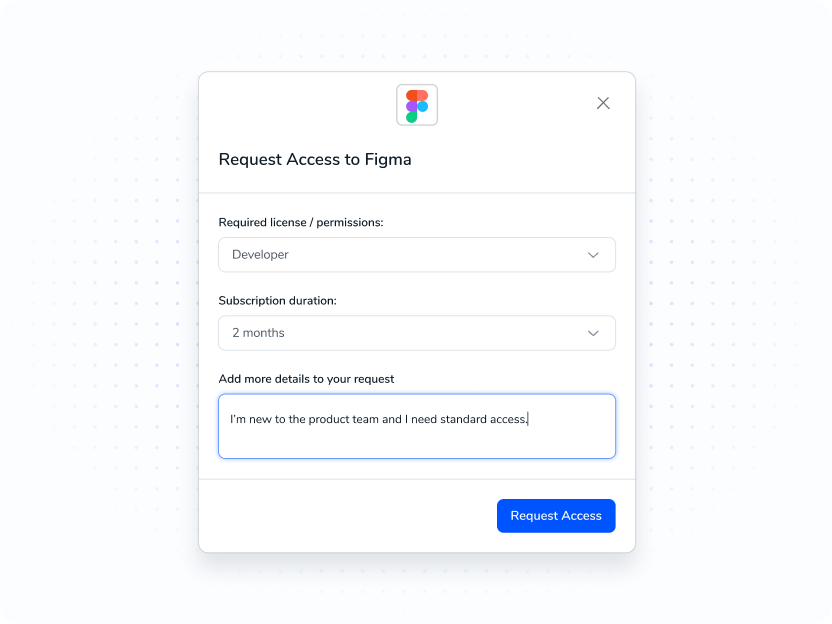
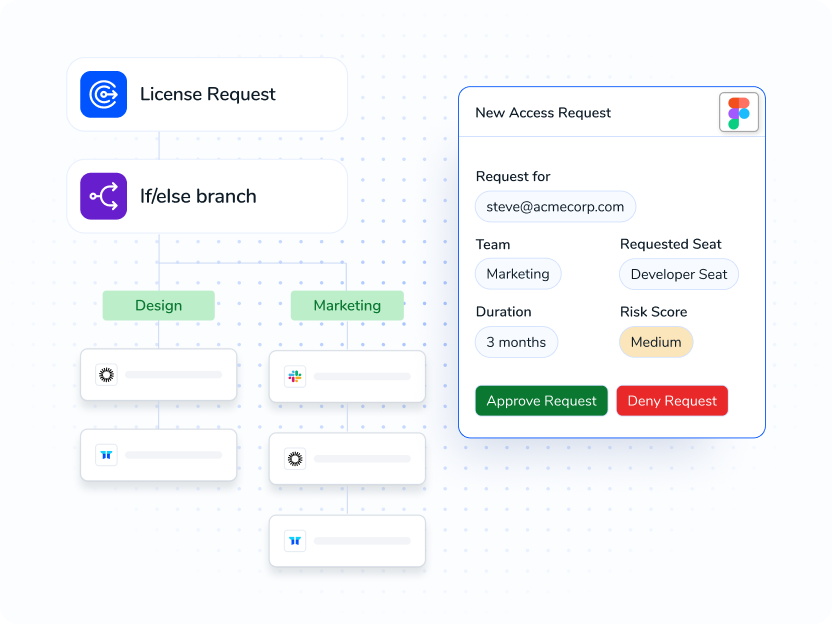
- Give the right access fast with policy guardrails and visibility into improper access.
- Guide requests in app or chat with owner routing, SLAs, and single or dual approvals.
- Fulfill and roll back across systems automatically with full evidence and an audit trail.
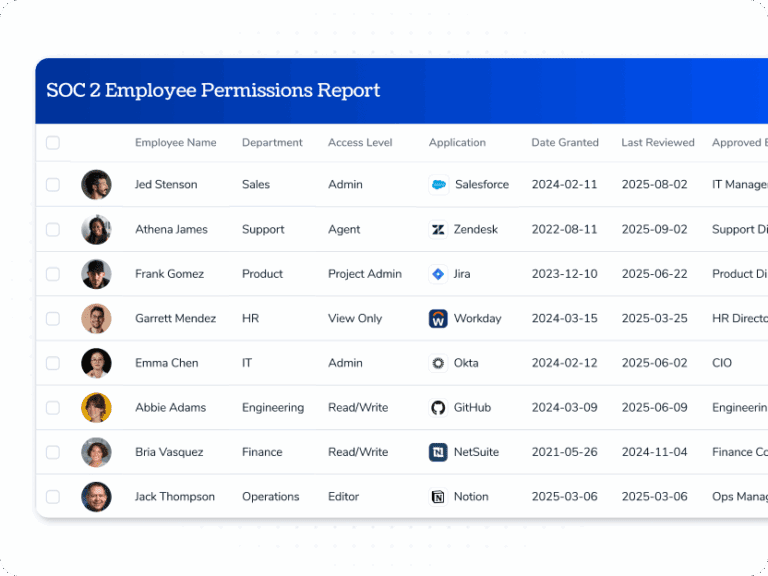
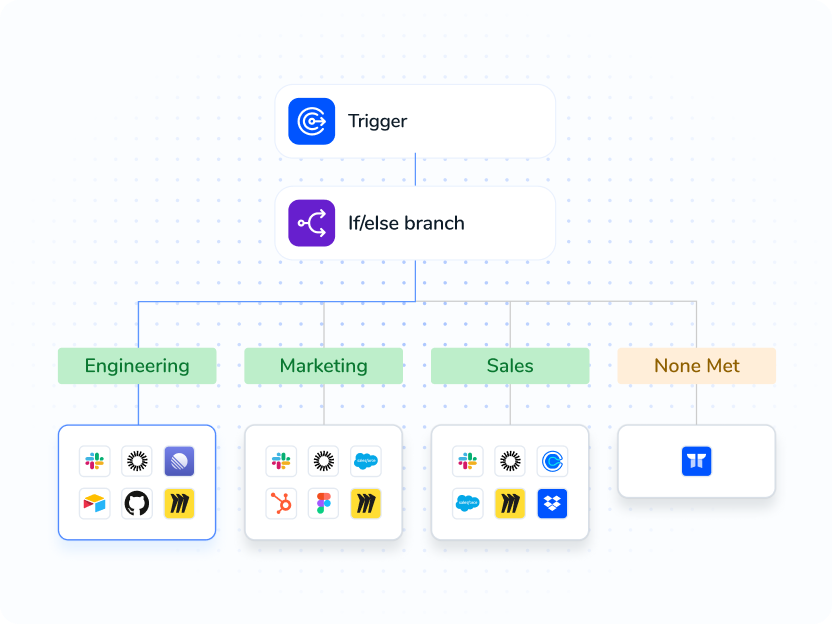
Automated Policy Enforcement
- Detect and prevent policy drift with continuous SoD and least-privilege checks.
- Auto-remediate dormant or risky access and open exceptions only when needed.
- Close certifications on time with in-place reviews and immutable evidence.
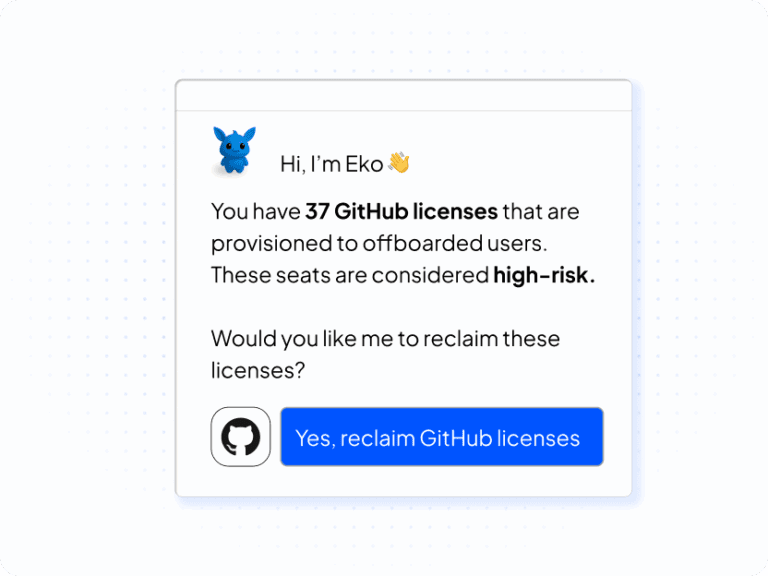
Eko — Agentic Governance Copilot
- Learns your policies and goals and prioritizes what moves risk, audit, and cost.
- Checks SoD and time bounds, routes approvals, and prepares safe rollbacks.
- Executes across systems with full evidence streaming to SIEM.
Get Full Control of your SaaS Stack, Finally
Complete certifications on time with in-place attestations, anomaly flags, routed ownership, and audit-ready evidence.
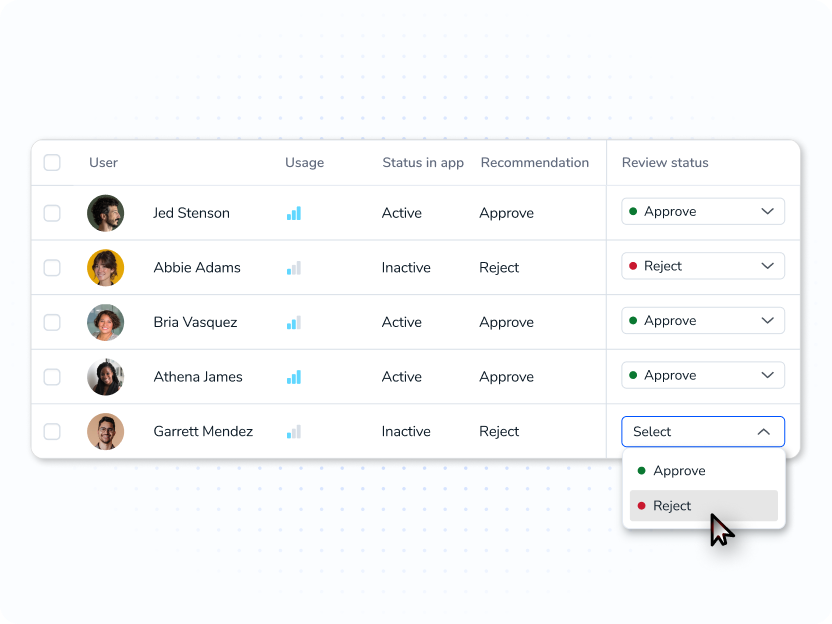
Guide requesters, route to approvers in chat or app, enforce SoD and time limits, and auto-fulfill with rollback.
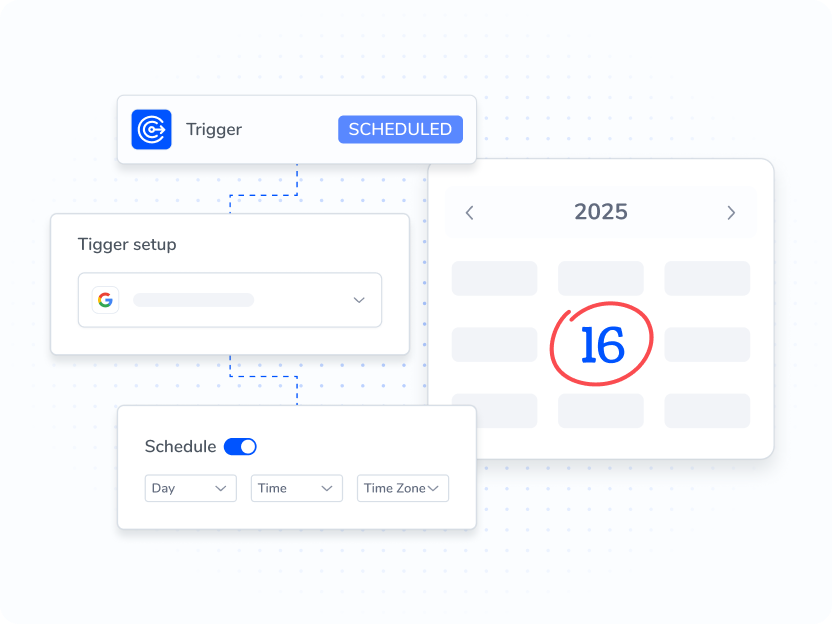
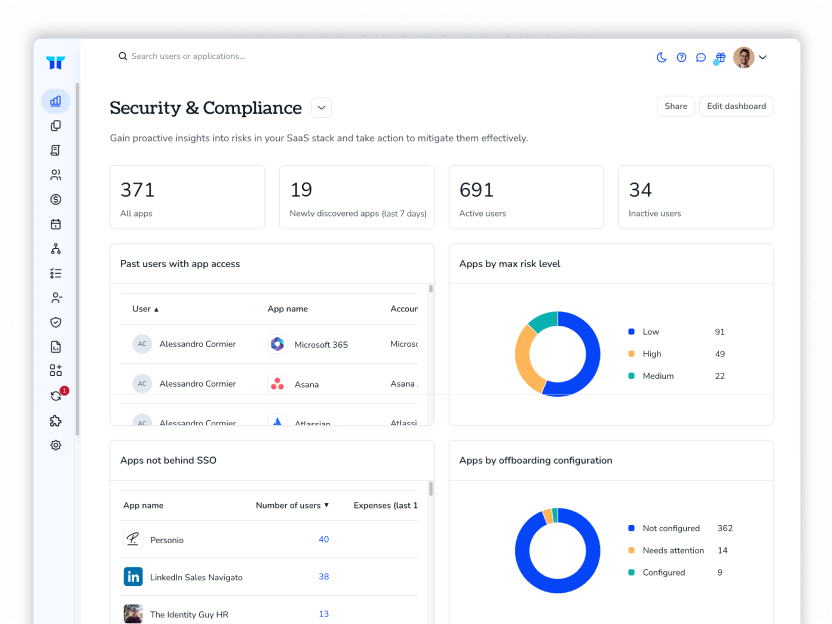
Track privilege changes and high-risk events in near real time with explainable alerts and evidence to SIEM.
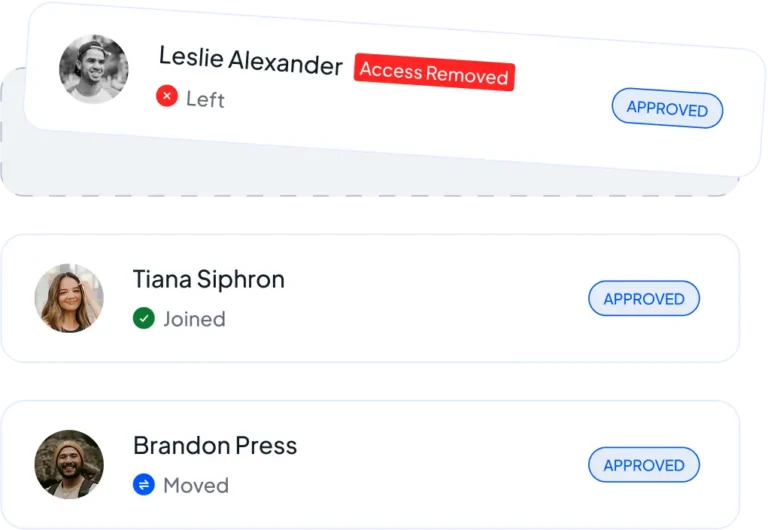
Automate joiner, mover, and leaver tasks with zero-touch offboarding, entitlement cleanup, and real-time evidence.
Right-size entitlements with usage insight and policy checks, then apply owner-approved changes.
Execute human-approved actions across your stack with full audit and one-click rollback.
Detect misconfigurations and toxic combinations, prioritize fixes, and verify remediation with evidence.
Fueled by the #1 Discovery and Automation Platform
Torii automatically connects known systems, discovers hidden ones, then prioritizes actions based on your goals, continuously enforcing identity and application governance.
Discovery & monitoring
Torii continuously discovers and monitors your stack and then prioritizes what matters
Automatic data ingestion
Connect once and Torii keeps identity, access, and usage data current and trustworthy.
Automatic governance
Actions execute across systems, evidence streams to your SIEM, and APIs & IaC let you automate at scale.
Outcomes You Can Prove
Visibility in hours across identities, accounts, apps, and AI
Audits closed on time with in-place certifications and immutable evidence
Scale governance without headcount

Seamlessly Integrates with Your Stack
Automatically ingest and standardize data from the tools you already use, keeping identity, access, and usage in near-real-time sync.
Comes with Enterprise Security & Control
Trusted worldwide since 2017. SOC 2 Type II, ISO 27001, GDPR compliant with SSO-only access, audit trails, and opt-out AI controls.

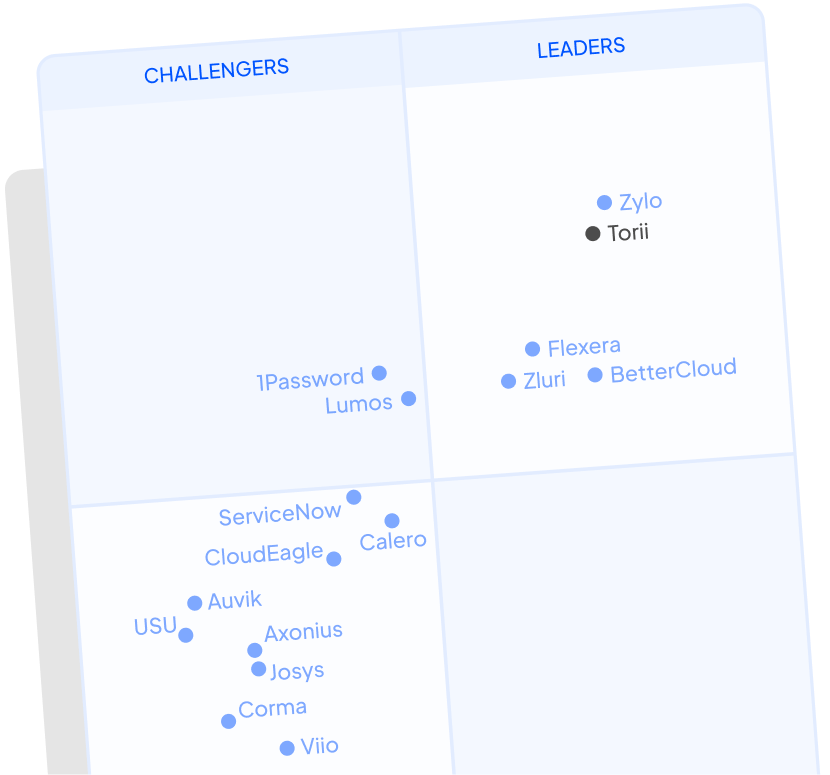
Torii is a Gartner® Magic Quadrant™ leader
Torii selected as a Magic Quadrant™ leader in the 2025 SaaS Management report.
Ready to Secure Your SaaS Stack?
Discover hidden apps, automate access reviews, and pass audits on autopilot.