Quick note: In this article, we discuss recent findings from a survey about the security threat posed by improper offboarding plans. If you want some resources right now, you can:
- Download our offboarding checklist
- Read the full survey report – Offboarding Security for a Remote Workforce
The Mass Offboarding
You’ve seen it in the news, you’ve read fourteen articles about it in Forbes, and maybe you’ve even participated in it: The Great Resignation.
This movement is not a good thing; it is not a bad thing. It simply is.
In this article, we won’t spend time fretting over who the next hire is, or retaining employees in the future. Instead, we will focus on how this resignation impacts the security of your organization due to the offboarding process.
You see, while the mass resignation isn’t good or bad, the offboarding process used by a company is good or (too often) bad. A good offboarding process doesn’t make the news because it happens in the background – out of sight. However, a poor offboarding process leaves the door open to enormous security risks.
Featured Video: How to Fix Your Offboarding Process [Explainer]
We know this because IT teams told us.
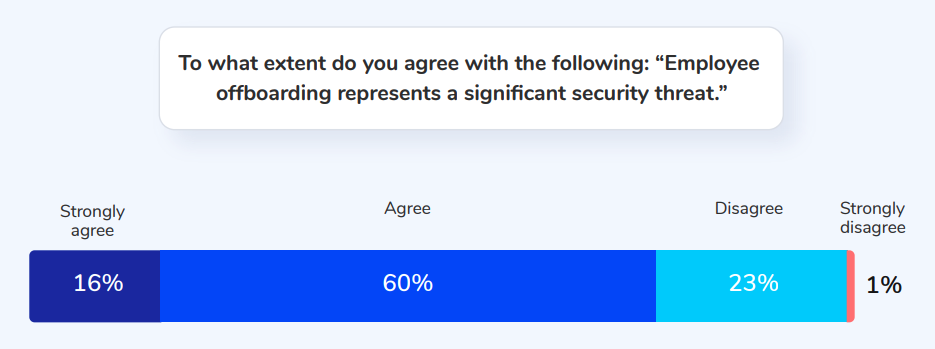
Security risk associated with poor offboarding processes is one of the top concerns for IT teams today. In a recent survey, we found that 76% of IT leaders agree or strongly agree that “employee offboarding is a significant security threat.”
📄You can read the full report here.
Offboarding is a long process that includes many considerations such as password managers, laptops, mobile devices, workplace keycards, and email forwarding. But, while all of those have a security risk component, survey respondents indicated that the biggest security threats stem from access privileges.
Why Access Privileges Present a Threat
When we talk about access privileges, we describe everything that a knowledge worker uses:
- Data
- Software
- Information
- emails
- Content
In a digital world (where so much of our work takes place online), letting a former employee keep access to their old work is like allowing them to keep a key for the office’s front door. Allowing that employee to keep their key would be unthinkable. Yet, we forget or fail to deprovision our employees from their digital workplace.
Now, there is one way in which a keycard and access privileges differ. A former employee won’t wander into their old worksite and cause problems by accident. But, they might “wander” into their old Google drive, email, or CRM and while that sounds innocent, it still includes risks.
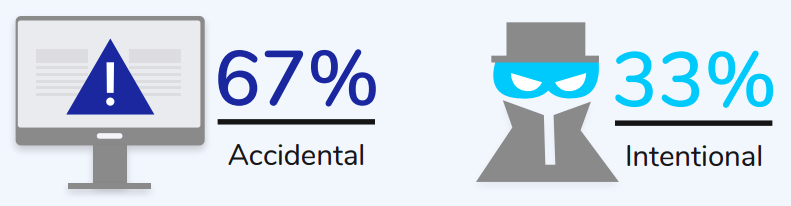
It is important to note that most IT professionals recognize that most breaches are not malicious. In the same survey, respondents said accidental breaches were of more significant concern – 67%. But, an accidental breach is still a breach and carries risks.
The Impact of the Pandemic
Not only did the pandemic result in “the great resignation,” but it also resulted in an increased remote workforce.
- Before the pandemic, in 2019, 5.7% of workers worked remotely 1
- In May of 2020, that number shot up to almost one in three 2
- Since then, the numbers have declined somewhat to around 26% 3
This shift to remote work has changed the calculus for IT on security threats.
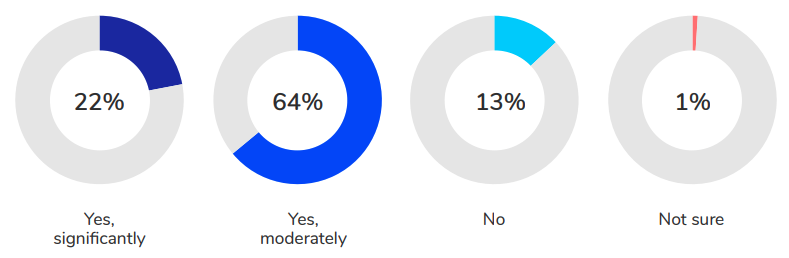
86% of survey respondents believe that the security threat landscape has changed due to the shift to remote work.
One of the significant changes is how many tools the employees now access.
The Growth of Application Adoption
At Torii, we wanted to know if the remote workforce resulted in more applications. So we dug into our data to find out.
Spoiler – It did increase – by a significant amount.
Before the pandemic, the average organization was adding approximately 14.4 applications per month.
🤔 Think that number sounds high? Unfortunately, there’s often a notable difference between perception and reality on this topic. Read the report to learn more.
During the Work From Home revolution (from February to September of 2020), that number averaged 21.6 applications per month. At one point during the spring, the number of new applications per month reached over 30.
After September, the number leveled out at around 18.5 new applications per month.
We can infer a few things from this data:
- During the peak of the pandemic, organizations were scrambling to find the right tools for their workforce
- Companies are still adopting applications at a faster rate than before the pandemic
- Broken offboarding processes are suffering even more now due to more applications
Let’s Review
So far, we’ve found that:
- 76% of IT leaders say, “Offboarding is a Significant Security Threat.”
- A majority of that threat is believed to be from access privileges
- These problems have become more complex in light of the Work From Home revolution
- The number of applications has increased throughout the last two years (and thus, so have access privileges left un-revoked)
So now the question is, what can we do with this knowledge?
How to Cut the Offboarding Security Threat of Access Privileges
Security threats will always persist thanks to threat actors, ransomware, and malicious efforts, but we’re addressing security threats due to poor processes, workflows, and protocols with offboarding. These are things that we can reduce or even eliminate.
The Power of a Checklist
Checklists are powerful because they keep us focused and honest. They provide a list of actions that we cannot (with a clear conscience) check off without completing the task. This format is perfect for two kinds of processes:
- Complex
- Mundane
For the IT team, offboarding a former employee is both complex and mundane. There is an element of complexity due to the sheer number of mundane tasks to do. In this regard, a checklist is a beneficial tool for maintaining proper offboarding protocols.
Not sure how to start developing an offboarding checklist for your IT team? We created one for you! Download Here
This checklist includes the ten critical steps for a smooth and easy employee offboarding process that will cover all your bases.
Checklists are excellent tools, but while they reduce the risk exposure, they don’t end them. Risk can persist due to a lack of knowledge.
The Importance of Application Insights
Insights and action are two sides of the same coin.
The outputs (actions) are ultimately dependent upon the quality of the inputs (knowledge). Therefore, when possible, our efforts must be informed by the data.
In the case of offboarding, we want to take action against security risks by de-provisioning access privileges. But, to do this well, we need the relevant insights – specifically – what can users currently access? What applications are they using? What spreadsheets do they access? What data sets do they interact with? You get the idea, but these questions are easier to ask than they are to answer. Self-reported information is unreliable, and Shadow IT means that users use far more applications than IT is aware of.
So how do we glean the critical information?
The Power of Discovery
Let’s review two facts we already discussed:
- Application adoption is constantly growing
- The number of applications IT knows about is chronically low relative to reality
Thus, IT needs better ways to discover the applications used throughout the organization.
Torii does that. Our discovery technology finds all the applications known and unknown that your company employs. Whether employees realize it or not, their SSO and email are associated with many tools. Don’t leave it to chance that you will find them all (because you probably won’t).
Discovery doesn’t just improve the quality of the offboarding process; it is essential to the process’s very success.
A checklist provides the protocol. Discovery provides insight. But what about the action?
The Power of Automation
Automation is a weighted word. Some hear a promise of utopia with no work. Others hear a dystopia with… no work. The reality is rarely so binary. Instead, automation takes on a specific kind of work, the rote-task-intensive work that we dislike. This automation does a couple of things for skilled workers:
- Allows us to focus on valuable work
- Removes the risk of user error common with boring or repetitive work
Let’s use the example of the offboarding checklist. Step number 2 of the checklist is “Close employees SaaS accounts.” Without a tool like Torii, not only do you have to figure out all the tools the employee used (sanctioned and unsanctioned), but you also have to go through and close or alter each of those accounts. Each SaaS application requires a slightly different process and many steps. These situations are the breeding ground for minor errors.
Torii, allows fully automated offboarding workflows. With our automated workflow, you can finally finish those never-ending tasks that linger and leave cracks in your security. Simplicity, efficiency, and peace of mind – all with one click.
If you would like to see our offboarding workflow in action, watch this short demo from our co-founder, Uri Haramati, as he demonstrates the power of Torii.
Conclusion
The great resignation has changed the way we think about the employee lifecycle and has brought attention to the potential security risks associated with mishandling that lifecycle. Access privileges, in particular, are a significant threat to security (even if the threats are due to accidental breaches). To combat these risks, IT teams need to; establish effective protocols, discover relevant information about application usage, and act on that knowledge. That action should also leverage automation to reduce the risks of user error common to repetitive tasks.
For your team, if you want to:
- Improve your offboarding process
- Reduce exposure to security threats
- Improve app discovery knowledge
- Spend less time on mundane tasks
Consider Torii for your SaaS Management.
Statistics:
1. https://www.rdniehaus.com/trends-in-remote-work-will-we-still-work-from-home-after-the-pandemic/
2. https://www.ncci.com/SecureDocuments/QEB/QEB_Q4_2020_RemoteWork.html
3. https://www.apollotechnical.com/statistics-on-remote-workers/
![[New Report] 76% of IT leaders say “Offboarding is a Significant Security Threat”](https://www.toriihq.com/wp-content/uploads/2021/12/IT-Checklist-for-Employee-Offboarding.png)