Your company doesn’t lack tools, but it might lack structure.
As the number of applications grows, so does the time and energy to keep those apps in line. Your team struggles to maintain visibility, enforce policies, and ensure quality data. The problem is that your stack feels more like a bucket of apps. You know that some are more critical than others, but the rest of the organization needs that framework. In this article, we’ll introduce a simple, three-layer hierarchy that you can use to bring structure and operational efficiency to your organization.
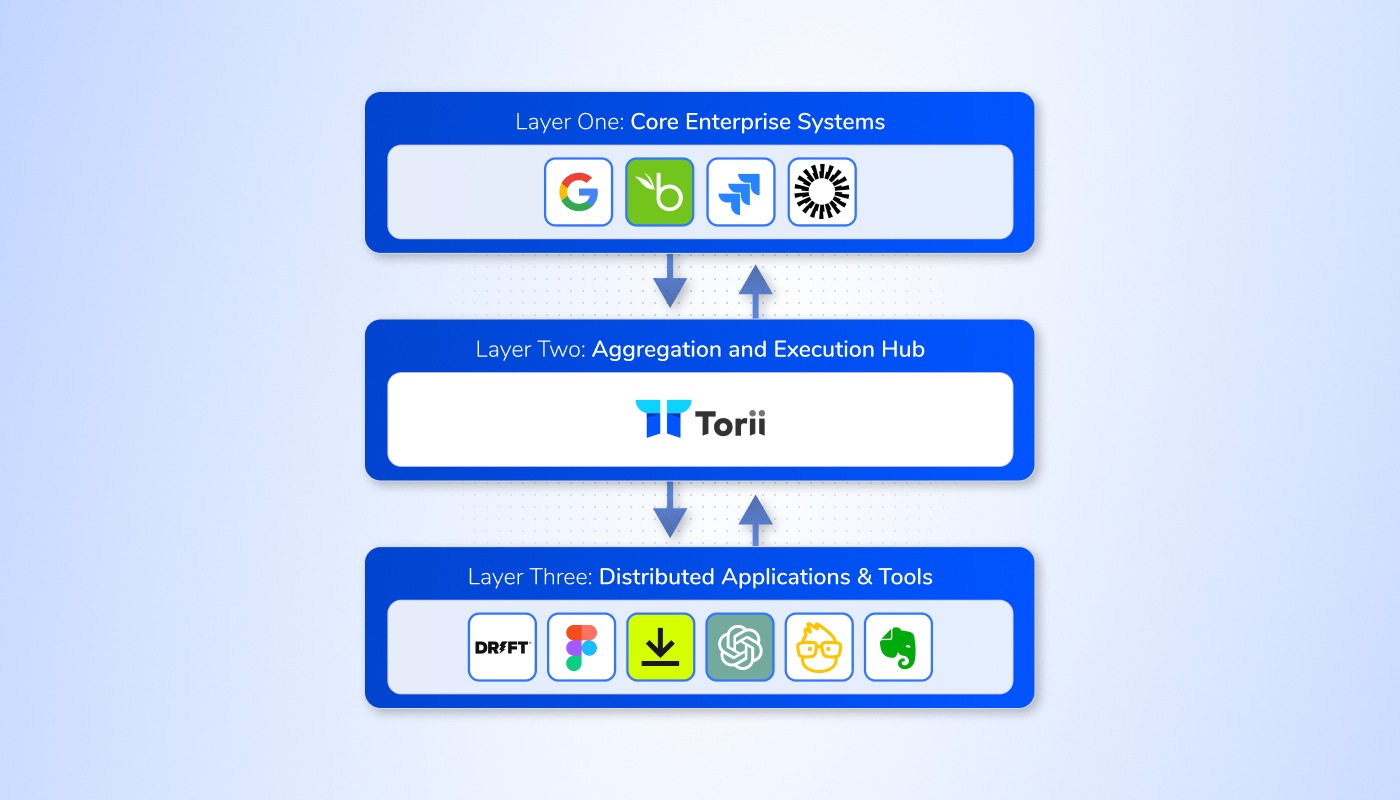
What Are the Three Layers of Your Application Hierarchy?
Your three layers are as follows:
Layer One: Core Enterprise Systems

These are your IdP, your SSO, your HRMS, your Contract Management System, your Financial App, and your CRM. The core systems are the sources of truth for the various departments in the organization. These tools set the policies and data standards for the rest of the tools in your organization.
Layer Two: Aggregation and Execution Hub

Most companies lack this layer, or they cobble together a patchwork of point solutions. But, mature organizations are starting to turn to SaaS management platforms to fill this need.
According to the Gartner Magic Quadrant for SaaS Management Platforms, an SMP tool will “help organizations discover, manage, optimize, and automate the SaaS application life cycle from one centralized console. ” The report goes on to say that “through 2027, over 50% of organizations will centralize SaaS application management using an SMP, an increase from less than 10% in 2024.”
Essentially, in today’s complex multi-cloud, digital workspace, organizations need a designated platform to enable governance at scale.
That platform must aggregate data from core systems and automate the permissions and actions of the rest of the apps. Below, we’ll discuss how a SaaS Management Platform makes this possible.
Layer Three: Distributed Applications & Tools

The remaining tools make up 90-95% of your applications. These tools include:
- Sanctioned tools for known uses
- Sanctioned tools for unknown uses
- Unsanctioned tools (shadow IT)
Some of these tools are local, but most are cloud-based. They are also virtually invisible to the IT department (not to mention procurement, finance, or security). Before you can manage these apps in any form, you must discover them.
Note about Application Discovery: App discovery is critical in stabilizing your IT ecosystem. With that data, governance is possible at scale. To learn more about executing a full application discovery process, check out this start-to-finish playbook.
Core apps focus on truth and data. Distributed apps, on the other hand, reflect that data. To control distributed apps, you first need to discover them. Once discovered, you can manage them in alignment with your core systems. For example, you define governance policies or employee lifecycle details in tools like Okta or HiBob. These details are then reflected across all relevant applications in the organization.
The problem is that most companies lack the unified vision and capabilities of an execution hub. This hub takes the details of core apps and, in the words of Jean-Luc Picard, “make it so” throughout all the apps in the organization.
How the Execution Hub Works
The execution hub represents the central integration and automation layer. It allows IT teams to manage their SaaS environments with control and precision. Torii, the market leader in SaaS Management, provides the capabilities to ensure every app interaction is governed, streamlined, and aligned with enterprise policies, providing the daily assurance of a hierarchical application ecosystem.
Here’s how Torii helps IT maintain control.
- Full Visibility of Cloud Apps: Torii provides complete app discovery for all organizations. It uses leading methods to uncover adoption, usage, costs, and other key details.
- MDM Integrations: Torii extends visibility to local apps through direct integrations with leading mobile device management tools (like Kandji, Intune, Jamf, and more). This approach provides a secure, complete view of SaaS and local software without extra device agents impacting security or performance.
- Extensive Integration Catalog: Torii includes over 170 built-in connectors for core applications. Many connectors also offer decisive actions and automation.
- ITSM Integrations: Service tickets, requests, and incident data flow seamlessly through Torii. It includes bi-directional support for Jira, ensuring IT and end-users interact smoothly.
- Webhook Triggers for Custom Actions: Torii lets you automate tasks from external systems. For example, you can trigger onboarding steps directly from a ticketing system.
- Custom Integrations via API: Connect on-premise and custom tools to unify license and user management.
- Policy Enforcement & Data Normalization: Torii standardizes information from core systems. It also flags anomalies to prevent inaccurate data from spreading to downstream applications.
- Open Platform: Build custom connectors and enrich dashboards with external data. This ensures a flexible, future-proof integration strategy.
With these capabilities, Torii bridges your core tools and the rest of your app ecosystem.
Security Considerations: Controlling Access and Reducing Risk
Security doesn’t always need complex tools. Sometimes, it’s about limiting how many people and systems interact with critical data. When too many individuals access core systems, errors spread, and unauthorized changes are harder to detect. Fewer touchpoints lower the risk of data mismanagement, operational inefficiencies, and potential breaches. Here are a few ways Torii improves GRC considerations related to your app stack.
Reduced Access Requirements: Torii is an automated intermediary between core and distributed apps. Under the direction of IT, instead of manually managing data in each distributed app, you use core apps to make updates and those changes. This simplifies workflows and improves control. With fewer direct access points, monitoring is more effective, and auditing is easier. Overall, this approach raises security standards without adding unnecessary complexity.
Risk-Based Monitoring: Beyond limiting access, Torii continuously evaluates each connected app’s risk profile. It considers factors like read/write privileges and data access to core systems. This ongoing assessment ensures you understand the
Compliance Certificate Insight: Torii also displays which apps have GDPR, SOC-2, and ISO 27001 certifications. You can use that compliance data as a trigger or a conditional branch in a GRC workflow.
Future-Proofing Your IT Ecosystem
As the organization grows and adds new tools, Torii acts as a stable middle layer. Instead of depending on every new app’s ability to connect directly to core systems, Torii maintains a consistent connection framework.
Whether switching financial platforms or adopting new identity providers, Torii’s flexible integration model means that changes at the top or bottom layers don’t disrupt the entire ecosystem.
What’s Next?
It’s time to reframe your IT environment. This isn’t a theoretical exercise—it’s a practical way to bring value and stability to your company. High-performing IT teams at companies like HiBob, Heap, and countless others have moved from SaaS sprawl to fully visible and managed SaaS stacks. They do this with the help of Torii in a matter of weeks and months, not years. By recognizing distinct tiers of importance and influence, you empower IT, procurement, Finance, and Security teams to make better decisions and enforce policy.
If you feel stuck in a swirl of apps, you need a structure and an execution layer. A solution like Torii sits at the crossroads of this hierarchy, turning the messy web of connections into a centralized bridge. Thus, you gain a single point of control over the data and orchestration of your app ecosystem.
Now is the time to explore the possibilities and learn how a comprehensive approach to discovery, integration, automation, and oversight can drive long-term stability. You’ll create a more secure, efficient, and future-ready IT environment.
Ready to learn more?